Archive
Forrester: 84% Of U.S. Adults Now Use The Web Daily, 50% Own Smartphones, Tablet Ownership Doubled To 19% In 2012
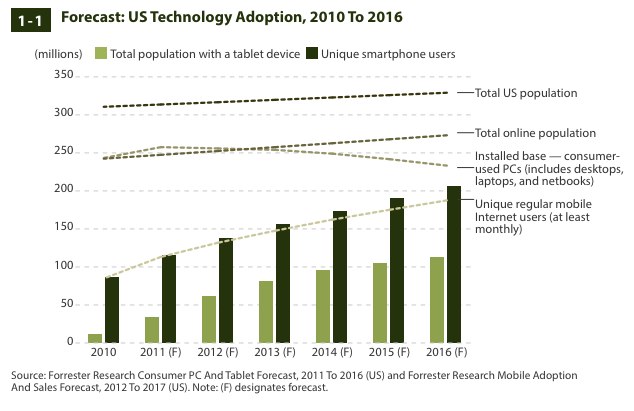
Forrester Research just published its annual “State of Consumers and Technology” report. As usual, it’s chock-full of interesting statistics about how U.S. consumers use the Internet, but the most interesting statistic is probably that the overall online penetration rate in the U.S. has stabilized at 79 percent (the same number Forrester found in 2011). That’s the percentage of U.S. adults that go online at least monthly. What has changed, however, is how many adults go online at least daily: In 2011, that was 78 percent of U.S. adults, and in 2012, Forrester reports that 84 percent now go online at least once per day.
One of the reasons for this is, of course, the growing smartphone and tablet penetration. Forrester found that about half of U.S. online adults now own a smartphone and two-thirds even own multiple connected devices. Tablet adoption doubled since 2011 and is now at 19 percent.
One trend that the Forrester report, which includes…
Continue reading here!
//Richard
#Citrix acquires #Zenprise to improve its BYOD capabilities
Wow!
I must say that this is a good move by Citrix! Citrix now gets access to one of the markets most extensive MDM solutions for mobile devices!
The whole story from Citrix has been;
DON’T manage the device, manage the apps and data!
But now I guess that Citrix realised that the need and ideas of many companies out there will require more management of the device and not just the delivery of the apps to it like you’d do with AppController (CloudGateway Enterprise).
So, hat off to this decision! 🙂
Read more about the news here;
Citrix Signs Definitive Agreement to Acquire MDM Leader Zenprise
And why not have a little look at these posts as well;
10 BYOD mobile device management suites you need to know
//Richard
New security threat at work: Bring-your-own-network
Computerworld – Even as IT pros wrestle with the bring-your-own-device (BYOD) trend, corporate security is being further complicated by another emerging trend: bring your own network (BYON).
BYON is a by-product of increasingly common technology that allows users to create their own mobile networks, usually through mobile wireless hotspots. Security professionals say BYON requires a new approach to security because some internal networks may now be as insecure as consumer devices.
Jim Kunick, an attorney with the Chicago law firm Much Shelist, said BYON represents a more dangerous threat to data security than employees who bring their own smartphones or tablets into the office. “The network thing blows this up completely, because it takes the data out of the network the company protects,” he said. “There’s no way to ensure the security of that data. People are running corporate apps and processing corporate and client data using networks that may or may not be secure.
“I mean, no one is sure the Boingo network is secure,” he said.
Continue reading here…
//Richard
AppSense MobileNow – BYOD, MAM
Ok, this is really interesting! What is AppSense up to when it comes to their new MobileNow and DataNow products? Are they simple understanding that they have to broaden their portfolio to find new market shares and are following the others like VMware with Horizon and Citrix with CloudGateway or are they trying to step up and try to take the lead and shortly add capabilities that the others have? Still I’m a bit puzzled and need to understand more…
But AppSense is not a huge corporation like Symantec so they could invest and try to speed up their capability development within this area… really interesting!
Here are some information about their MobileNow product:
BYOD Done Right
MobileNow is the first and only solution architected from day one to solve the complete Bring-Your-Own-Device (BYOD) problem for both IT and employees. It delivers real-time security, control and compliance for IT and a seamless experience and freedom of choice – apps, data, and devices – for executives and employees. Unlike status quo MDM-only solutions, MobileNow doesn’t require you to take complete control over and manage employees’ personal devices, apps and data. And unlike proprietary “container” and SDK-based solutions, MobileNow doesn’t limit users to only a small number of proprietary apps.
Fire Your CIO
Ok, yet another interesting article!
“The following post is by Mike Abramsky, principal of Red Team Global , which facilitates technology innovation via collaborative workshops and consulting.
Do you stifle productivity – or shoot the CIO?
That’s the dilemma increasingly faced by CEOs. With the rise of tablets, smartphones, social media, apps and personal clouds, we are in the midst of a profound computing shift, perhaps the greatest technology revolution in the enterprise since the invention of the PC. But the IT department with its risk-averse, slow-moving, heavy-handed culture threatens to torpedo hoped-for productivity.
This revolution is more than just technology; some CEOs recognize it as early days of Retooling the Enterprise. The ease of adoption of these new tools means non-technical staff can pursue faster, more flexible”
Continue reading here…
//Richard
Mastering the BYOD trend: The ultimate guide
Have a look at this BYOD guide and get inspired! 😉
“Let’s face it: The BYOD trend is a big deal.
IT admins have questions about the influx of personal smartphones and tablets in the enterprise. They worry about it. And they often need help figuring out what to do about bring your own device (BYOD) management, security and application delivery.
It takes a combination of technology, policy and organization-wide strategy to maximize the benefits of a BYOD program and minimize the risks. This comprehensive guide explains the basics and offers helpful, in-depth tips for admins stuck at any level of a BYOD program.”
Continue reading here!
//Richard
Mobile Application Management (MAM) = Complete Mobile Workplace?
Ok, so I’ve been looking at some of the players out there that say they have a “MAM” product and everybody seem so hooked on talking about MAM and how that’s gonna solve all the needs of a Mobile Workplace… and to be totally frank I think that people tend to run to fast with new cool and hip buzz-words or solutions.
To start of with, what is the definition of a MAM system? This is a pretty good summary I’d say that I stole from WikiPedia;
“Mobile Application Management (MAM) describes software and services that accelerate and simplify the creation of internally developed or “in-house” enterprise mobile applications. It also describes the deployment and management of in-house and commercially available mobile apps used in business settings on both company-provided and “bring your own” smartphones and tablet computers.
Mobile application management has also been defined as “the strategy and process around developing/procuring, securing, deploying, accessing, configuring, updating and removing (business) applications from mobile devices used by the employees. To read more at wikipedia click here…”
And does a solution like this provide all the capabilities for businesses today for a complete Mobile Workplace?
Microsoft Security Newsletter – September 2012
Ok, didn’t have the time to search where online the newsletter is located so I just copied some of it into this post. I think that there where some interesting posts/articles around “BYO”, Cloud etc. So browse and enjoy! 😉
| Welcome to September’s Security Newsletter! |
This month’s newsletter focuses on personal devices in the workplace, often times referred to as “Bring Your Own Device,” or BYOD. BYOD is a very hot topic these days as organizations grapple with the challenge of managing the risks involved in allowing corporate data to be placed on personal devices such as smart phones. At face value, BYOD has the potential to be a win-win proposition. However, depending on how BYOD is implemented and managed, it could be a Pandora’s box.The primary challenge is that some of the devices employees decide to bring to work may not have basic security or management capabilities. This challenge is compounded by the risks associated with connecting to social networks and by the diverse ways organizations and people are choosing to connect and share data today – such as the utilization of cloud services. We recently conducted a study to find out more about how personal devices are being used in the business environment. Our study found that:
BYOD does have distinct advantages. From the standpoint of the IT department, BYOD is generally seen as a cost-cutting measure because the burden of supplying the equipment is shifted to the employees. Some organizations subsidize BYOD policies with a per diem to offset the costs for users, but it still results in lower costs for the organization by relieving IT of its traditional role of maintenance and support. Another advantage of BYOD is that individuals tend to upgrade and embrace new platforms and technologies much faster than businesses. The organization benefits from being able to take advantage of cutting edge tools and features without the pain of deploying new hardware to the entire company. From the user’s perspective, BYOD means using devices and applications that are more familiar. Empowering users with the ability to choose which hardware and platforms they use creates more satisfied and productive workers. It also allows them to carry a single mobile device instead of one for work and another for personal use. The list of smart personal devices capable of connecting to private and public networks is rapidly and constantly expanding. For chief information security officers (CISOs) and chief security officers (CSOs), managing an ever growing list of devices and applications isn’t a sustainable model. Some of the security professionals I have talked to are shifting their focus to managing the data instead of the devices. They have concluded that device security is only a proxy for data security; if they can’t effectively manage the security of the devices that employees bring to work, they will focus on managing the security of the data itself. I think the industry recognizes the importance of securing personal devices and are making steps toward better management controls in the future. If you are interested in learning more about BYOD, I encourage you to read these blog posts recently published on the topic:
|
BYOD = reality or just a vision? – Part 2
Ok, where did we end part 1.. yes, it was around my personal view around why it’s not that easy for enterprises to adopt a BYOD concept similar to what we at EnvokeIT have.
(If you haven’t read part 1 you can do that here.)
So why can we work this way and not the enterprises, well there are many answers to that question. One reason may be that they have IPR etc that is important to protect and a legacy IT environment that has been around since the mainframe era with a lot of in-house developed apps, it’s a legacy that we newcomers don’t have! And they also have a much more complex organization with difference roles and requirements. It’s sometimes hard to tell a developer to work on any device with no development tools installed locally and only work in a remote desktop which requires him/her to be online. These users would perhaps want to be able to perform their development work from their vacation cabin up north with limited connectivity or wherever they can’t be connected. And the whole world doesn’t have the connectivity that we in europe are used to.
BYOD = reality or just a vision? – Part 1
BYOD – Bring Your Own Device – Part 1
Consumerization of IT, BYOD, BYOC and all the fuzz about that we shall and already have started to use our personal devices at work, or that our employer doesn’t provide us with a company asset anymore. So many definitions and models, it’s like asking someone what the definition of Cloud is. You’ll get all the different answers about what a ‘Private’, ‘Public’ and ‘Personal’ Cloud is etc. But where are we really?